An elliptic curve over a finite field is defined by the Weierstrass standard equation:
Where and are constants that determine the shape of the curve.
These type of curves are used on crypto-systems like ECDSA (Elliptic Curve Digital Signature Algorithm) due to the difficulty of solving the ECDLP (Elliptic Curve Discrete Logarithm Problem).

1. Elliptic curves in cryptography
Elliptic curves have gained popularity over classical methods such as RSA because they offer an equivalent or superior level of security with significantly shorter key sizes. For example, a 256-bits key on ECDSA offers a security level comparable to 3072-bits RSA key (See Table 2 of NIST SP 800-57 Part 1 Rev. 5)1. This results in significant savings in bandwidth, computational time, and storage space. Additionally, the ECDLP (Elliptic Curve Discrete Logarithm Problem) is considered harder to solve than the classical DLP (Discrete Logarithm Problem) in integers modulo . As a result, with equal computational resources, elliptic curves provide a higher level of security.
2. Group structure in Elliptic Curves
For the construction of the algebraic structure used in ECDSA, we must define an abelian group over the curve.
2.1 Definition of an Abelian group
An abelian group is an algebraic structure (), where:
- is a non-empty set
- is a binary operation defined
Which satisfies the following properties:- Associativity:
- Identity element:
- Inverse element:
- Commutativity:
2.2 Construction
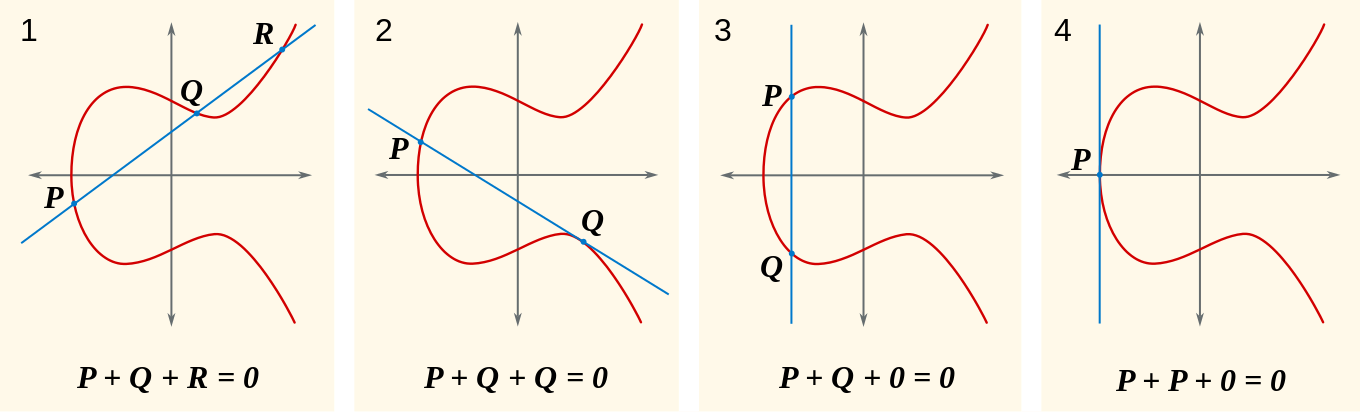
Over these elliptic curves, we define the algebraic structure of an abelian group as follows: Let be an elliptic curve over a field defined by the Weierstrass standard equation
where and the curve is non-singular (i.e., it has no points with multiple tangents).
Consider the points and such that
The binary operation is defined as follows:
If and :
- Calculate the slope between and
- Calculate coordinates of the point
Thus:
If : the slope between and is the derivative of the curve at :
Taking the derivative:
Substituting gives:
We define a point at infinity on the projective plane, this point satisfies the following properties:
If and then:
The point serves as the neutral element, ensuring the structure is an abelian group.
Scalar multiplication in this structure is defined as follows: Given a point and a scalar :
3. The security of Elliptic Curves: ECDLP (Elliptic Curve Discrete Logarithm Problem)
The security on this signature scheme relies entirely on the ECDLP, which is defined as follows:
- Given an elliptic curve over the finite field , a generator point on the curve, and a point on the curve, find the integer such that
For carefully selected finite fields, there is not efficient solution to this problem.
Scalar multiplication on an elliptic curve over a finite field is analogous to exponentiation in the multiplicative group (Integers modulo ), for example:.
mirrors the operation in
Thus, the ECDLP is analogous to DLP (Discrete logarithm problem) in .
However, the best known algorithms for ECDLP have roughly exponential complexity, unlike DLP in some groups where subexponential algorithms are known. As a result, breaking ECDLP is widely believed to be harder at equivalent key sizes.
Note that the difficult of ECDLP depends largely on the size of the field and the rigorous selection of the curve, such as secp256k1.
4. Cryptographic keys in Elliptic curves
4.1 Private keys
Private keys are integers selected within the range of the curve size, generally are integers of 256-bit. The generation of these keys is extremely fast and efficient.
4.2 Public keys
The public keys are points on the elliptic curve, defined by their coordinates . Due the properties of this family of curves, the points can be expressed in a compressed format using only a single coordinate and a flag indicating whether is positive or negative. Therefore, a 256-bit private key corresponds to a 257-bit public key.
4.3 Generator and order
On an elliptic curve , a point (generator), an integer (order) are defined; represents the number of points over the curve. For a generator , there exists an such that where . This is called the order of the subgroup generated by . is a generator of the entire group if .
4.4 Key derivation
Given a elliptic curve and a generator point , let be an integer (Private key). It is possible to compute a point on the curve.
This operation consists of summing the point with itself times.
Note that calculate given the points and is computationally infeasible because:
- There is no defined inverse operation in the group that allows
- The only known methods to determine are through brute force or specialized algorithms, ensuring the security of the system.
This process is described in greater detail in Digital Signature Standard (DSS)2
5. ECDSA: Digital signatures with Elliptic Curves
It is important to use well-known and rigorously selected elliptic curves to avoid security breaches, such as the widely used secp256k1.
Below, we outline the ECDSA algorithm, based on Practical Cryptography For Developers3
5.1 Generation
The process for signing a message is as follows:
- Compute the hash of the message () with SHA-256 (Secure Hash Algorithm)
- Generate a random integer in the range where is the order of the curve.
- Compute the point . Take the coordinate of the point and assign it to
- Calculate the signature proof:
where is the modular inverse of satisfying and is the private key of the signer.
- The signature is the pair
5.1.1 Considerations
Note that if the random number is generated with low entropy—meaning it is predictable or reused—the system becomes vulnerable to leaking the signer’s private key.
5.2 Verification
To verify the signature, the message , the public key and the signature are taken as input. The process is as follows:
- Compute the hash of the message () using SHA-256 (Secure Hash Algorithm)
- Compute the modular inverse of the signature proof
- Attempt to recover the random point used during the signature. Define:
- Take the coordinate of the recovered point as
- The signature is valid if .
It is also possible to recover then public key from the signature.
5.2.1 Considerations
Note that finding and through brute force is totally infeasible.
5.3 Implementation
The following is an example of the ECDSA algorithm implemented in Solidity.
function verifySignature(bytes32 message, uint8 v, bytes32 r, bytes32 s) public view returns (bool) { bytes32 hash = sha256(abi.encodePacked(message)); return ecrecover(hash, v, r, s) == msg.sender;}6. Conclusion
The elliptic curves offers high security and efficiency for cryptographic purposes due to their algebraic-geometric structure, which complicates the development of algorithms capable of solving the ECDLP quickly. On the other hand, ECDSA uses shorter keys than other equivalent systems, such as RSA, which has made ECDSA a standard in the cryptography industry.
6.1 References
Footnotes
-
NIST, “Recommendation for Key Management: Part 1 – General (Rev. 5),” NIST Special Publication 800-57 Part 1 Rev. 5, 2020. [Online]. Available: https://doi.org/10.6028/NIST.SP.800-57pt1r5. ↩
-
NIST, “Digital Signature Standard (DSS),” Federal Information Processing Standards Publication 186-4, Section 6, pp. 15-22, July 2013. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-4.pdf. ↩
-
Svetlin Nakov, “ECDSA: Sign and Verify Messages,” Cryptobook, [Online]. Available: https://cryptobook.nakov.com/digital-signatures/ecdsa-sign-verify-messages. [Accessed: Dec. 12, 2024]. ↩